A (usually) plaintext password. Passes only if the given
password matches that sent in the Access-Request. If CHAP-Password
attribute appears in the request then CHAP authentication will be
attempted. If MS-CHAP-Challenge and MS-CHAP-Response attributes appears in
the request then MSCHAP authentication will be attempted. CHAP and MSCHAP
authentication is only supported with plaintext or Rcrypt encrypted
passwords. You may user either Password or User-Password as the attribute
name, the effect is the same.
Radiator also supports HTTP Digest
password authentication with plaintext passwords. Digest authentication is
supported by some web servers (e.g. Apache) and some web proxies (e.g.
squid).
User-Password can be in a number of formats, not necessarily
in plaintext. Radiator looks for some special format passwords and
interprets them as special encryptions. The following formats are
supported, along with example versions of the password "fred".
- Standard Unix crypt.This format is also compatible with Unix
password encryption as used in Netscape LDAP server. Passwords
starting with a leading {crypt} or {CRYPT} are interpreted as a
standard Unix crypt password, using the native version of crypt() on
your platform.
User-Password = {crypt}1xMKc0GIVUNbE
- Linux MD5 password hashing. Passwords starting with "$1$" are
interpreted as hashed with Linux MD5 password hashing.
User-Password = $1$cTpht$Obu9PLSMst1TDou.mN5bk0
- Linux SHA256 and SHA512 crypt. Passwords starting with “$5$” or
“$6$” are interpreted as hashed with Linux SHA256 or SHA512 password
hashing, respectively.
User-Password =
$5$cTpht$i4ihNcS7lC1orrwWu/IfHrhxdDIkjBu095szYO4AucD
User-Password = $6$cTpht$Z2pSYxleRWK8IrsynFzHcrnPlpUhA7N9AM/
8O8se885W45WHyJ2K6bXsygHI46.cjqgl2hucmKtX1shWTL1zU1
- Linux Blowfish crypt. Passwords starting with $2a$, $2x$ or $2y$
are interpreted as hashed with Linux Blowfish password hashing.
Support for these algorithms depends on the system crypt()
implementation support. See the system documentation on crypt() about
caveats with these hashes.
- Netscape SHA password hashing as used in Netscape LDAP server.
Passwords starting with {SHA}, {SSHA}, {sha}, or {ssha} are
interpreted as being hashed with Netscape SHA hashing. (Requires
Digest-SHA version 5.0 or later, and also Mime::Base64 from
MIME-Base64-2.11.tar.gz).
User-Password = {SHA}MQF6ciZl5K/OWGlQ9ClEptMx2r8=
User-Password = {SSHA}k1qAjger6rE9fhCrig+QPZ/HTrJhYWE=
- SHA-2 hashes SHA 256, 384 and 512. These are similar to {SHA} and
{SSHA} above. See
goodies/sha.pl and
goodies/ssha.pl for a utility to generate
hashes.
User-Password =
{SHA256}0M/C5TGbgs3HGjOHPoJsk9fuETY/iskcT6Oiz80ihuU=
User-Password =
{SSHA256}abN9UTbhi3evQvdk7uYNML+UMZn8/BnWdxJUApQ0NzGkLQTd
User-Password ={SHA384}QoAkviNtBCtNyjN+yAkEEL6ChjtUVFKDTKHrIlx/
YqIHrDG7Tx2eJhbBPKAX0mo5
User-Password =
{SSHA384}DLZqetLxS6JPok1QcugKji0U8lxt6Zq7SYoGoK5JRVeeOqCuGHwxXf
1ZYGLg8pXqgms3jw==
User-Password = {SHA512}NWbDPDXFm6JYe6wqgVJs8z6gkoER7Z4WFqpD/
P+8P10H4FjICJjNKGCVt1h61e3TUR/ZQ/19d0Ox3tckJiAm8w==
User-Password =
{SSHA512}u+34y2JyCKoVRty0ADABlzhETpPv1HnShr2427qjsn7tgSoOaP8cHB
J95GT28ENlA7vySsjBVOMiuPqk2qgPvJOV4IM=
- MD5 Hex digest. Passwords starting with {MD5} or {md5}. Note that
all hex digits are required to be lower case.
User-Password = "{MD5}570a90bfbf8c7eab5dc5d4e26832d5b1"
- MD5 with Mime, as used in some other LDAP servers.
User-Password = "{MD5}qP0OV/oViFka8YbFMWEWeg=="
- Rcrypt reversibly encrypted passwords. This reversible encryption
format depends on a secret key. Radiator includes a reusable code
module (Radius::Rcrypt) with encrypt and decrypt routines that you can
call from third party programs. Rcrypt passwords require that you
define the RcryptKey attribute in the AuthBy clause. The leading
string can be {rcrypt} or {RCRYPT}.
User-Password = "{rcrypt}nYXkJKLrxm/e3RfU0aT7w4al"
- A predigested hex MD5 signature of the concatenation of the user
name, a realm and the correct password. This is only valid for Digest
and SIP authentication. In this example, the user name is "mikem", the
realm is "open.com.au" and the correct password is "fred".
User-Password = \
"{digest-md5-hex}884663db69c36190cf4c05c068a1a303"
- MySQL hashed password, as produced by the MySQL password()
function.
User-Password = "{mysql}0569ef75321b8fed"
- MD5 hashed password in the format used by old Netscape Mail
Servers.
{NS-MTAMD5}
b6b49e37d494a09bfde663033274bc83cd1bf318fa32c5866166a7edcb1
e1c87
- A Django style password. For more information, see User authentication in Django
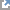
User-Password =\
"sha1$a1976$065f52b49153328da76e13c2b462b860a70eb78b"
User-Password = "md5$a1976$e67d1ca20e9c28321b86e34076cc48ab"
- DEC Hashed Password as used by DEC VMS and maybe others. Contains
the algorithm type number, a salt and the hashed password, separated
by vertical bars. The valid algorithm numbers are 1 (PURDY), 2
(PURDY_V) or 3 (PURDY_S) The hashed password depends on the user name
as well as the algorithm and salt, so the hashed passwords are not
portable between users. In VMS, user names are by convention all
uppercase, and passwords are case sensitive. In this example for user
name MIKEM, the algorithm type number is 3 (PURDY_S), the salt is
1234, and the hashed password (fred) is 85ad61e72a41dec4.
User-Password = {dechpwd}3|1234|85ad61e72a41dec4
- An NT Hashed Password, as used by Microsoft, Samba and others.
This format is compatible with Samba SMB passwords (either in a flat
file or in LDAP). Such password hashes can be generated with the Samba
mkntpwd program.
User-Password = {nthash}DCB8E94AC7D0AADC8A81D9C895ACE5F4
- A password encrypted with the Microsoft SQL
pwdencrypt() function. Passwords encrypted with
pwdencrypt() are case insensitive. Requires
Digest::SHA module. Note that the encrypted password produced by
pwdencrypt() is a 46 octet binary string. Radiator
recognises the encrypted password as either 46 octets of binary or 92
octets of ASCII Hex characters. You can use the MS SQL ‘+’ string
concatenation operator to prepend the ‘{mssql}’ to the encrypted
password, e.g.
select '{mssql}' + password, ..... from .....
User-Password =
{mssql}01003A54FC73501798169BEC84C05CA0D2FBB70009C2556313DA7959
C1A798ECD34514694A13D29ED57BE9CBE5DA
- A flagged plaintext password.
User-Password = {clear}fred
- A PBKDF2 (Password-Based Key Derivation Function 2) derived
password. Radiator currently supports password derivation with Pseudo
Random Function (PRF) HMAC-SHA1 and the following password format
(PRF:rounds:salt:hash). See
goodies/pbkdf2.pl for
the format details. Requires
MIME::Base64.
User-Password = {PBKDF2}HMACSHA1:
9000:h9Pwh4tcu0w=:iN9vitCZ1mqBKEu21dlc0RW2tlc=
- Custom format for CheckPasswordHook. For more information, see
Section 3.32.23. CheckPasswordHook.
User-Password = {OSC-pw-hook}.......
- Plaintext. Any other format is interpreted as a plain text
password.
User-Password = fred
User-Password = "password with spaces"