attrname attrnum type [flags]ATTRIBUTE Service-Type 6 integer
stringtextstringintegersigned-integerinteger8integer16integer64dateipaddripaddrv6ipaddrv4v6binaryabinaryhexadecimalbooleantagged-integer
tagged-string
ipv4prefixipv6prefixifidtlvcustomattrnum may be in decimal, hex (prefixed
by ‘0x’) or octal (prefixed by 0).ATTRIBUTE Tunnel-Password 69 string has_tag,encrypt=2
has_tagencrypt=n (n = 1, 2 or 3)
attrname valuename valueVALUE Service-Type Login-User 1
value may be in decimal or hex (prefixed by
‘0x’).vendornum attrname attrnum type
[flags]VENDORATTR 9 cisco-avpair 1 string
attrnum may be in decimal, hex (prefixed
by ‘0x’) or octal (prefixed by 0).attrname attrnum type [flags].vendorname vendornumber vendorname
[parent=attributename]END-VENDOR are to be interpreted as
VENDORATTR definitions for the named vendor.parent=attributename syntax is needed when
Vendor-Specific attributes from extended space, as defined by RFC 6929,
are used. The following example shows how to define a Vendor-Specific
Attribute named OSC-Uid and an Extended-Vendor-Specific
Attribute named OSC-Extended-Example. These both use
Vendor-Id 9048 and
Vendor-Type 1. The full "dotted
number" notation that uniquely identifies
OSC-Extended-Example is
241.26.9048.1. The unique identifier of
OSC-Uid Vendor-Specific Attribute is
26.9048.1.VENDOR OSC 9048 VENDORATTR 9048 OSC-Uid 1 string BEGIN-VENDOR OSC parent=Extended-Vendor-Specific-1 ATTRIBUTE OSC-Extended-Example 1 string END-VENDOR
format=attributename is also allowed. The exact syntax
used by different implementations is still
evolving.filenamefilenamedictionarydictionary.ascenddictionary.* and
goodies/dictionary.*radiusd code.DictionaryFile parameter to load the dictionaries as
separate files.DictionaryFile parameter in your configuration
file. See Section 3.7.16. DictionaryFile.radiusd expects to find it before starting
radiusd. You should also be careful to specify the
same dictionary to radpwtst with the -dictionary
argument if you use it for testing.builddbm and
buildsql utility to create a DBM user database. See
the users file in the Radiator distribution for an
example.Attribute = Value, and it defines a RADIUS attribute
that is checked in Access-Requests before the user is authenticated.
Multiple check items are separated by commas. There must be no comma after
the last check item in the line. Values may optionally be surrounded by
double quotes, which are ignored. For more information about check items,
see Section 7. Check and reply items.mikem is granted
access, the modem is configured for Framed-Protocol of PPP, and IP netmask
of 255.255.255.0, Framed-Routing of None and a Framed-MTU of 1500.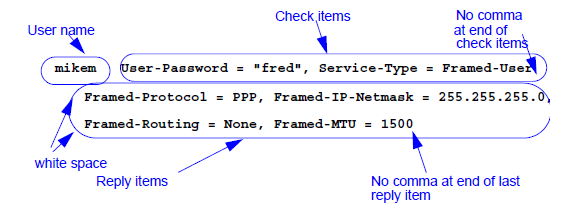
builddbm).builddbm utility, and you can also use
builddbm to print the attributes for a particular
user. You can convert a DBM user database into an SQL database with the
buildsql utility./etc/password on Unix implementations
that do not use a password shadow file. It will work with
/etc/shadow on Unix implementations that do use a
password shadow file (Radiator will need to run as root to get read access
to /etc/shadow).
time:seconds:user:submitted_password:correct_password:result
Mon Jun 29 12:24:21 1999:899087061:mikem:fredd:fred:FAIL Mon Jun 29 12:24:38 1999:899087078:mikem:fred:fred:PASS Mon Jun 29 12:38:53 1999:899087933:mikem:fred:fred:PASS
# Users can log into ports 1-10 and 21-30 inclusive # on 10.1.1.1 or into ports 100 to 115 inclusive on # 10.1.1.2, or into ports 16 to 20 inclusive on # mynas.domain.com 10.1.1.1 1-10 10.1.1.1 21-30 10.1.1.2 100-115 mynas.domain.com 16-20 # For iPASS roaming: 0.0.0.0 0-1000
<AuthBy FILE> uses these groups and the group
file is defined with GroupFilename parameter. For
more information, see Section 3.35.2. GroupFilename.Admin-group username1 WiFiClient-group username1, username2, username3 Readonly-group username4, username5